In today’s interconnected digital world, Application Programming Interfaces (APIs) are the hidden gems that enable seamless data exchange and communication between systems and applications. However, this very connectivity makes APIs a prime target for cyber threats. The broad landscape of API design patterns and consumer types complicates security requirements for organizations.
Securing your API ecosystem is not just a technical concern but a strategic imperative. This can be accomplished with a strong focus on API Governance and integrating the different security practices that I will explain in each of the API Lifecycle stages. Let’s dive into the main areas of focus for API security without getting lost in the technical weeds.
Secure Design and Development of API Ecosystem
When it comes to API ecosystem security, a solid foundation is crucial. To start, consider industry-standard guidelines like the OWASP API Security Top 10. This serves as an excellent starting point for organizations, providing a list of evolving threats that should be on your radar.
The security design review process is a critical step. It involves threat modeling to identify potential threats to your systems and determine appropriate countermeasures. This process becomes more complex when dealing with 3rd party dependencies and partner ecosystems, which are common scenarios in today’s API-driven world. To stay agile, streamline and automate your threat modeling processes as much as possible.
Once security requirements are defined, translate them into coding and configuration practices, focusing on areas such as authentication, authorization, input validation, and encryption. Establish secure practices that explicitly address these areas and make them an integral part of your API Governance strategy.
API Documentation
API Documentation is not just a technical necessity; it impacts various aspects of your organization, from design reviews to security testing. Surprisingly, many companies struggle to keep their API documentation up-to-date.
According to the Salt State of API Security report for Q1 2023, a mere 9% of companies update their primary APIs daily. This API documentation gap, also known as API drift, can lead to discrepancies between what’s documented and what’s actually in production.
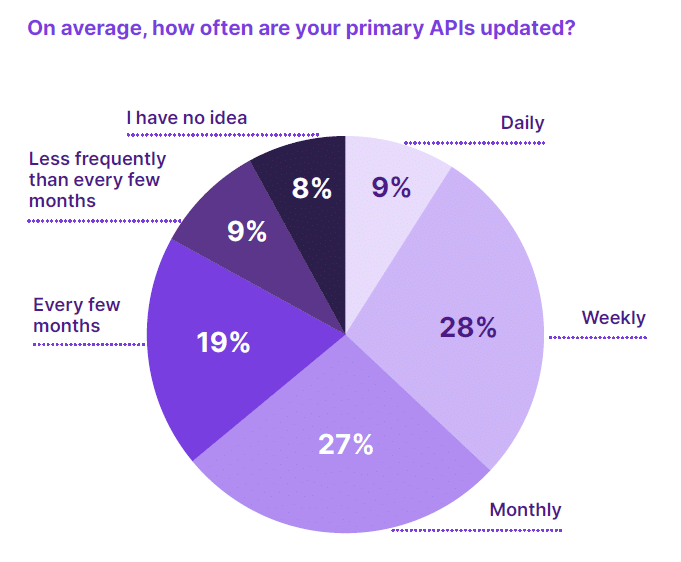
This gap in API documentation, also known as API drift, leads to a mismatch between the current state of APIs in production and what is expected or documented. The only way to address this gap is to monitor your production environments or seek tooling that can auto-discover APIs, auto-generate schema definitions, and produce an API inventory. Unfortunately, respondents to the cited Salt report said that their confidence in a complete and accurate API inventory is low, with only 19% saying they feel very confident. 34% are either not at all or not very confident. And 43% fall somewhere in between, saying that they are somewhat.

Once again, API Governance comes to the rescue of API Ecosystem here. Setting documentation-related constraints that should be checked before promoting APIs between environments can be a good idea. API schema validators can find common issues related to formatting or overlooked parameters while Spectral rulesets allow to implementation of more complex validations. If these validations fail, the API won’t be promoted.
API Discovery and Cataloguing to Build a Resilient API Ecosystem
In today’s complex IT landscape, APIs are often scattered across various systems and services. Automated discovery tools can help identify these endpoints, making it easier to manage and secure them. In addition, it also should include the ability to catalog the parameters and data types used in your APIs as their understanding is crucial for effective security.
However, a comprehensive API inventory is not only essential for security but also for compliance and risk assessment (focus on securing high-risk APIs and endpoints first to minimize potential threats).
Finally, regulatory bodies often require organizations to provide detailed information about their APIs.
Security Testing
Security testing should encompass a range of strategies, including vulnerability scanning, penetration testing, and code reviews. These approaches help identify and remediate security weaknesses in your APIs.
One of the issues of paramount importance when considering security testing is automation, especially when the API ecosystem is considerably wide. Leverage automated testing tools to streamline the security testing process. These tools can identify common vulnerabilities and ensure that security measures are consistently applied.
On the other side, security is an ongoing process, and APIs are continually evolving. Implement continuous security testing to detect and address new threats and vulnerabilities as they emerge.
Logging and Monitoring
Logging and monitoring should capture a wide range of data, including authentication attempts, request rates, geographic origins of requests, accessed data stores, and more. This data provides insights into system activity and security threats.
Once collected, the data plays a crucial role in incident response as it enables your organization to detect and respond to security incidents promptly, and to establish baselines for analyzing general system performance and availability issues when anomalies in these baselines happen.
API Mediation and Architecture
APIs also have some impact on your enterprise architecture and, although this article is far from being technical, it is worth mentioning how API Gateways (the component in charge of handling API calls) work. Understanding the role of API gateways is essential for a secure architecture.
Simply put, API gateways act as intermediaries between external clients and your APIs. They provide a layer of mediation, security, access control, and many others that allow your organization to apply customized runtime policies to your APIs.
Network Security
Traditional network perimeters are eroding as organizations adopt cloud services and distributed architectures. Understanding this shift is vital for modern network security strategies.
Best security practices on network security are based on the so-called zero trust principles: access to resources is based on authenticated context and behavior within a session, not network location. Note that this approach is essential for securing distributed API ecosystems.
Ensuring Data Security in API Ecosystem
Data security aims to provide confidentiality, integrity, and authenticity of data. This means ensuring that data is kept private, unaltered, and trusted by using the following techniques:
- Anonymization and Pseudonymization: Depending on data security goals and regulations, consider techniques like anonymization and pseudonymization to protect sensitive information.
- Encryption: Encryption is a fundamental data security measure. Implement it both in transit and at rest to protect data from unauthorized access.
- Credential Protection: Be aware that attackers may target credentials or authorized sessions to access data. Implementing robust credential protection measures is essential.
Conclusions
API security is not just a technical concern but a strategic imperative, and it’s your responsibility as CIO to verify that your organization is embracing these best practices to secure your API ecosystem, protect your data, and ensure the trust of your customers.
To conclude, let me highlight my main advice:
- Prioritize API Security: Make API security a top-level priority in your organization’s digital strategy. Allocate the necessary resources and expertise to protect your API ecosystem.
- Invest in Education: Ensure that your teams, from developers to IT administrators, are well-versed in API security best practices. Knowledge is your best defense.
- Implement API Governance: Enforce documentation standards and security practices across the organization. This ensures consistency and reduces the risk of vulnerabilities.
- Stay Informed: The threat landscape is constantly evolving. Stay informed about emerging threats and adapt your security measures accordingly.
By taking these steps, you not only protect your organization from cyber threats but also pave the way for a secure and successful digital future.
More articles from David Roldán Martínez:
PSD3: Unleashing the Power of Open Finance – The Evolving Landscape and Top Priorities for CIOs
Harnessing the Potential of AI in Banking
The Synergy Between AI and APIs: Enabling AI as a Service and Revolutionizing API Management

Expert in APIs, AI, Digital Transformation, Business Solutions, and Open Economy related sectors. I bring a unique blend of technical and business expertise to the table. With a proven track record of delivering successful solutions for businesses of all sizes, I have helped organizations develop innovative business solutions by understanding their pain points and challenges and designing a roadmap to overcome them and drive growth.
My extensive experience in APIs at all levels has enabled me to work on a variety of complex projects, from building custom integrations to managing complex API ecosystems. I have a deep understanding of the intricacies of the API landscape.









